成功拦截CVE-2021-40444漏洞利用,安芯网盾提醒做好安全防护
近日,安芯网盾内存安全产品帮助客户实时拦截了CVE-2021-40444漏洞利用。该漏洞CVSS评分为 8.8 分,是Windows MSHTML中的一个远程代码执行漏洞。
安芯网盾研究人员对该漏洞利用进行了复现,如下是在不同模式下的拦截结果呈现:
1.拦截模式:在发现风险的第一时刻进行拦截,阻断恶意代码的后续行为。
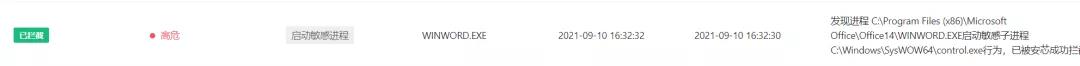
2.仅上报模式: 如果设置了仅上报模式,则可以监控整个恶意行为链。
该样本触发漏洞后,通过控制面板命令行(control.exe)加载恶意载荷:

进而创建rundll32.exe,执行恶意载荷,通过WMI与远端服务器通信:
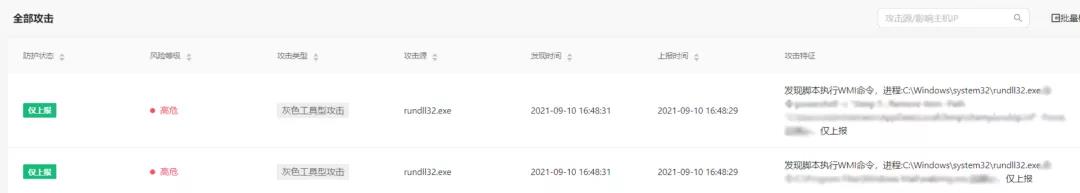
行为分析:
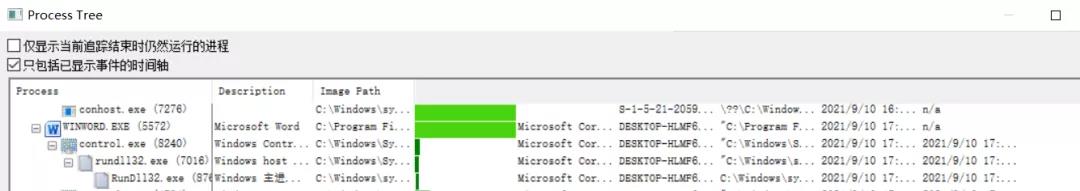
安芯网盾安全研究人员分析之后发现,该POC是一个docx文档:
首先通过下载远程的
http://hidusi.com/e8c76295a5f9acb7/side.html,
加载含有漏洞的Microsoft MSHTML模块,触发漏洞。
然后下载
http://hidusi.com/e8c76295a5f9acb7/ministry.cab。
在ministry.cab中释放出可以链接远端CS服务器的恶意载荷:championship.inf;
最终通过rundll32.exe执行,与恶意服务器通信,达到远控目的。
漏洞防御措施:Microsoft MSHTML引擎存在远程代码执行漏洞,攻击者可通过制作带有恶意 ActiveX 控件的Microsoft Office文档并诱导用户打开此文档来利用此漏洞。成功利用此漏洞的远程攻击者可在目标系统上以该用户权限执行任意代码。受影响的主机操作系统版本包括:
- Windows 7 for x64-based Systems Service Pack 1
- Windows 7 for 32-bit Systems Service Pack 1
- Windows Server 2012 R2 (Server Core installation)
- Windows Server 2012 R2
- Windows Server 2012 (Server Core installation)
- Windows Server 2012
- Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation)
- Windows Server 2008 R2 for x64-based Systems Service Pack 1
- Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation)
- Windows Server 2008 for x64-based Systems Service Pack 2
- Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation)
- Windows Server 2008 for 32-bit Systems Service Pack 2
- Windows RT 8.1
- Windows 8.1 for x64-based systems
- Windows 8.1 for 32-bit systems
- Windows Server 2016 (Server Core installation)
- Windows Server 2016
- Windows 10 Version 1607 for x64-based Systems
- Windows 10 Version 1607 for 32-bit Systems
- Windows 10 for x64-based Systems
- Windows 10 for 32-bit Systems
- Windows Server, version 20H2 (Server Core Installation)
- Windows 10 Version 20H2 for ARM64-based Systems
- Windows 10 Version 20H2 for 32-bit Systems
- Windows 10 Version 20H2 for x64-based Systems
- Windows Server, version 2004 (Server Core installation)
- Windows 10 Version 2004 for x64-based Systems
- Windows 10 Version 2004 for ARM64-based Systems
- Windows 10 Version 2004 for 32-bit Systems
- Windows Server 2022 (Server Core installation)
- Windows Server 2022
- Windows 10 Version 21H1 for 32-bit Systems
- Windows 10 Version 21H1 for ARM64-based Systems
- Windows 10 Version 21H1 for x64-based Systems
- Windows 10 Version 1909 for ARM64-based Systems
- Windows 10 Version 1909 for x64-based Systems
- Windows 10 Version 1909 for 32-bit Systems
- Windows Server 2019 (Server Core installation)
- Windows Server 2019
- Windows 10 Version 1809 for ARM64-based Systems
- Windows 10 Version 1809 for x64-based Systems
- Windows 10 Version 1809 for 32-bit System
安芯网盾的内存安全产品基于硬件虚拟化等前沿技术针对0day漏洞利用提供高等级的安全保护,通过细粒度的监控内存访问行为,结合分析模块,可实时检测内存破坏型漏洞和逻辑型漏洞,并进行响应。目前,鉴于此漏洞已被检测到在野利用且漏洞POC及EXP已公开,此漏洞的现实威胁进一步提升,安芯网盾建议受影响的客户尽快自查并采用措施缓解此漏洞。















