
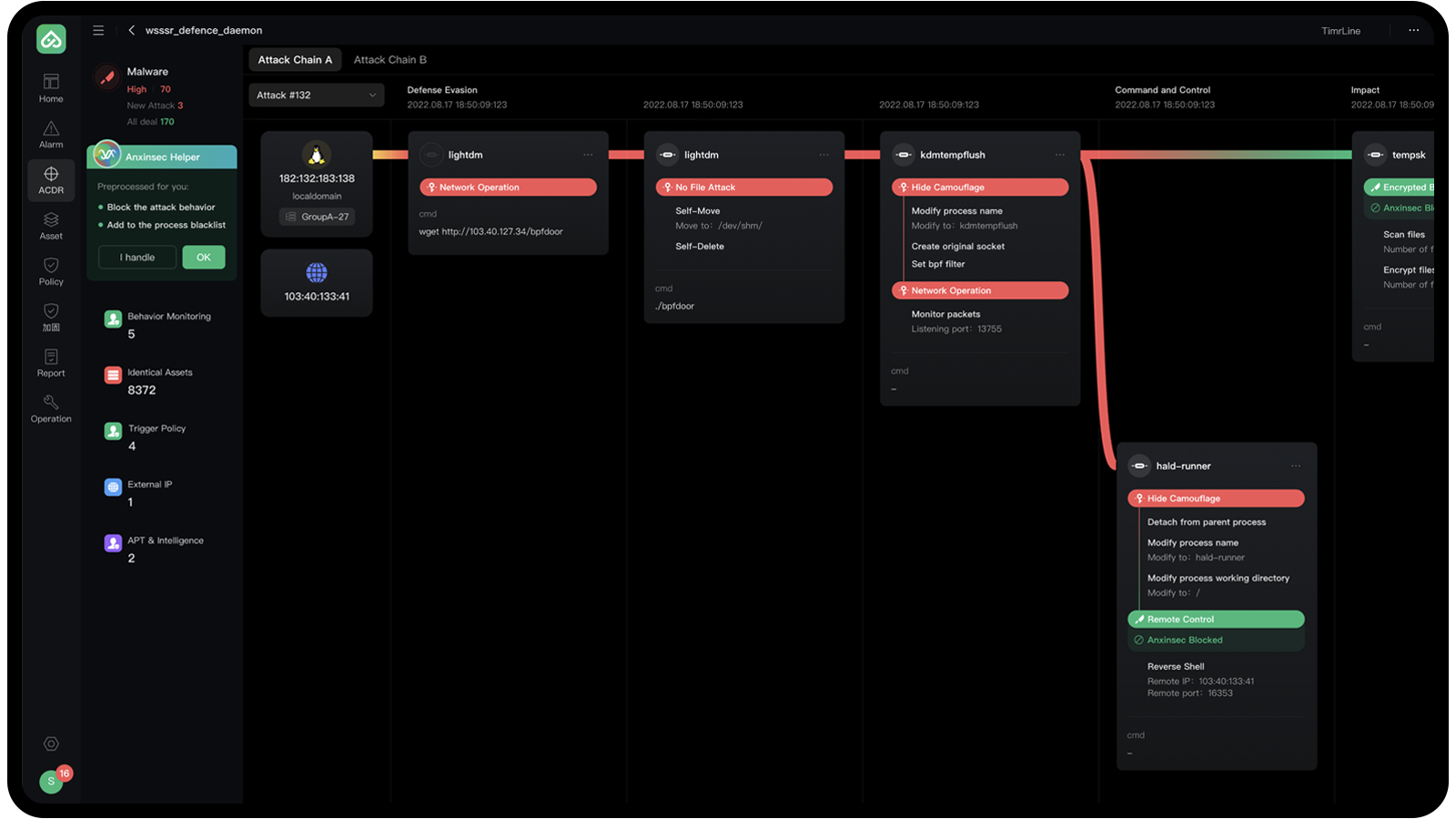
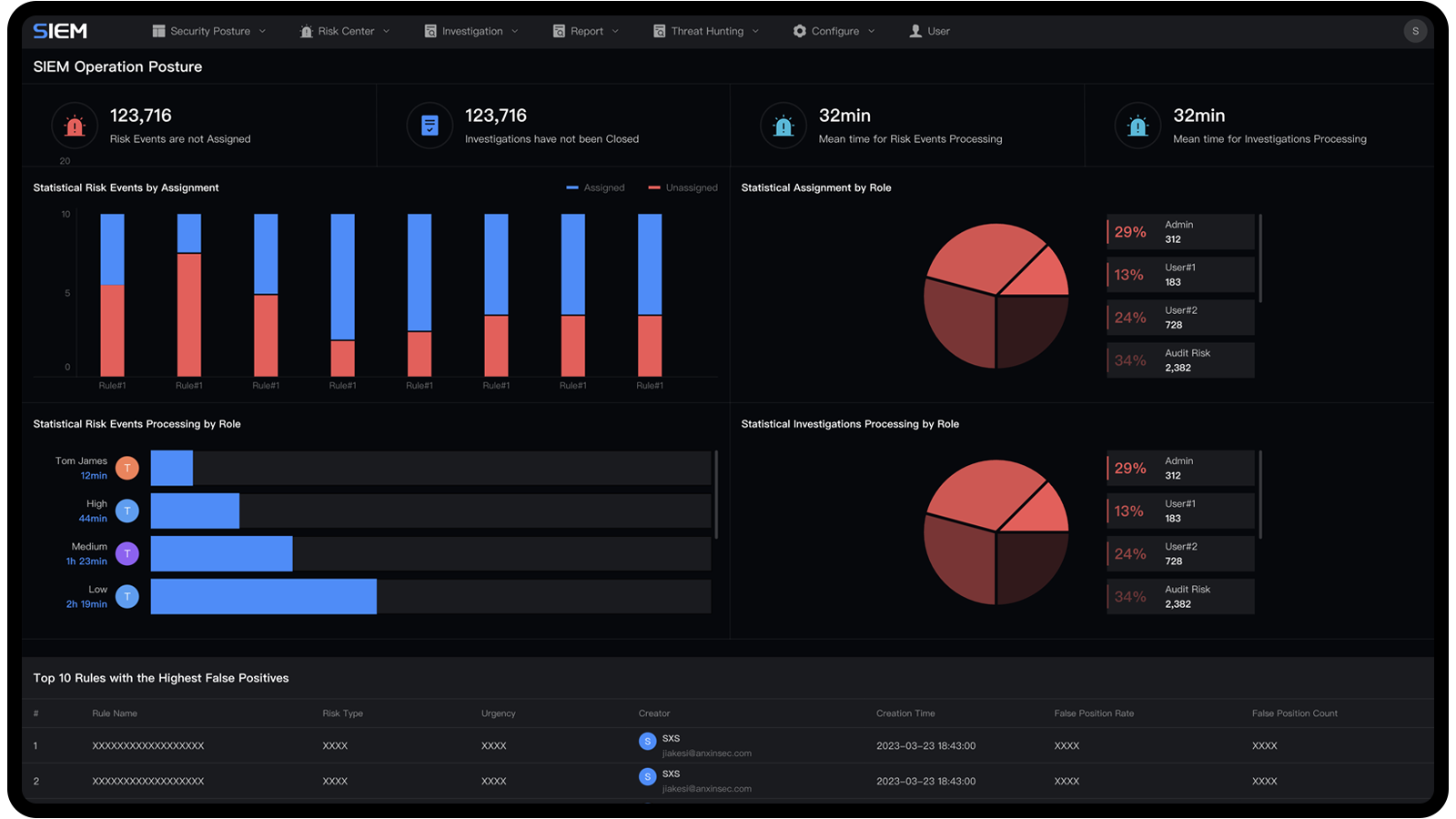
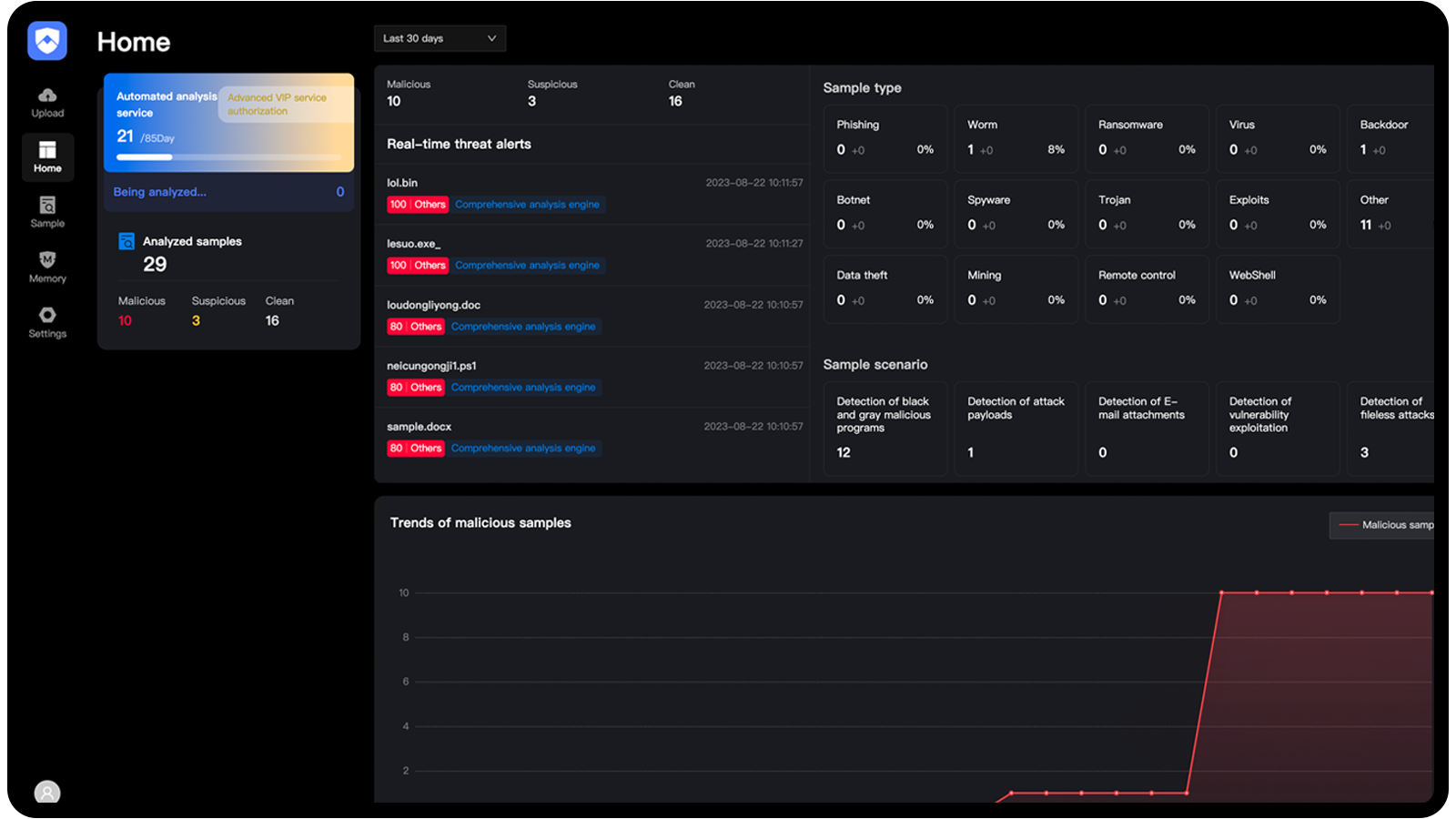



















With comprehensive strengths manifested in aspects such as technological innovation and prominent achievements in the field of memory security, Anxinsec has received many awards and honors from the China Cybersecurity Industry Alliance (CCIA), including "Star of Potential in China Cybersecurity in 2020," "Award of Excellence in Cybersecurity Innovation Products in 2020," and "Highest Investment Value Award of Cybersecurity Innovation Products in 2020," among many others.


Virtualization technology technologyies can monitor the reading, writing, and executing behavior of memory, which could prevent unusual memory access , malicious code execution and various other attacks, forging a complete and secure memory security environment for computer systems.
Although the high technological barriers of the underlying hardware instruction dictate the scarcity of players, it is the ultimate weapon against unknown threats.

With comprehensive strengths manifested in aspects such as technological innovation and prominent achievements in the field of memory security, Anxinsec has received many awards and honors from the China Cybersecurity Industry Alliance (CCIA), including "Star of Potential in China Cybersecurity in 2020," "Award of Excellence in Cybersecurity Innovation Products in 2020," and "Highest Investment Value Award of Cybersecurity Innovation Products in 2020," among many others.


Virtualization technology technologyies can monitor the reading, writing, and executing behavior of memory, which could prevent unusual memory access , malicious code execution and various other attacks, forging a complete and secure memory security environment for computer systems.
Although the high technological barriers of the underlying hardware instruction dictate the scarcity of players, it is the ultimate weapon against unknown threats.
