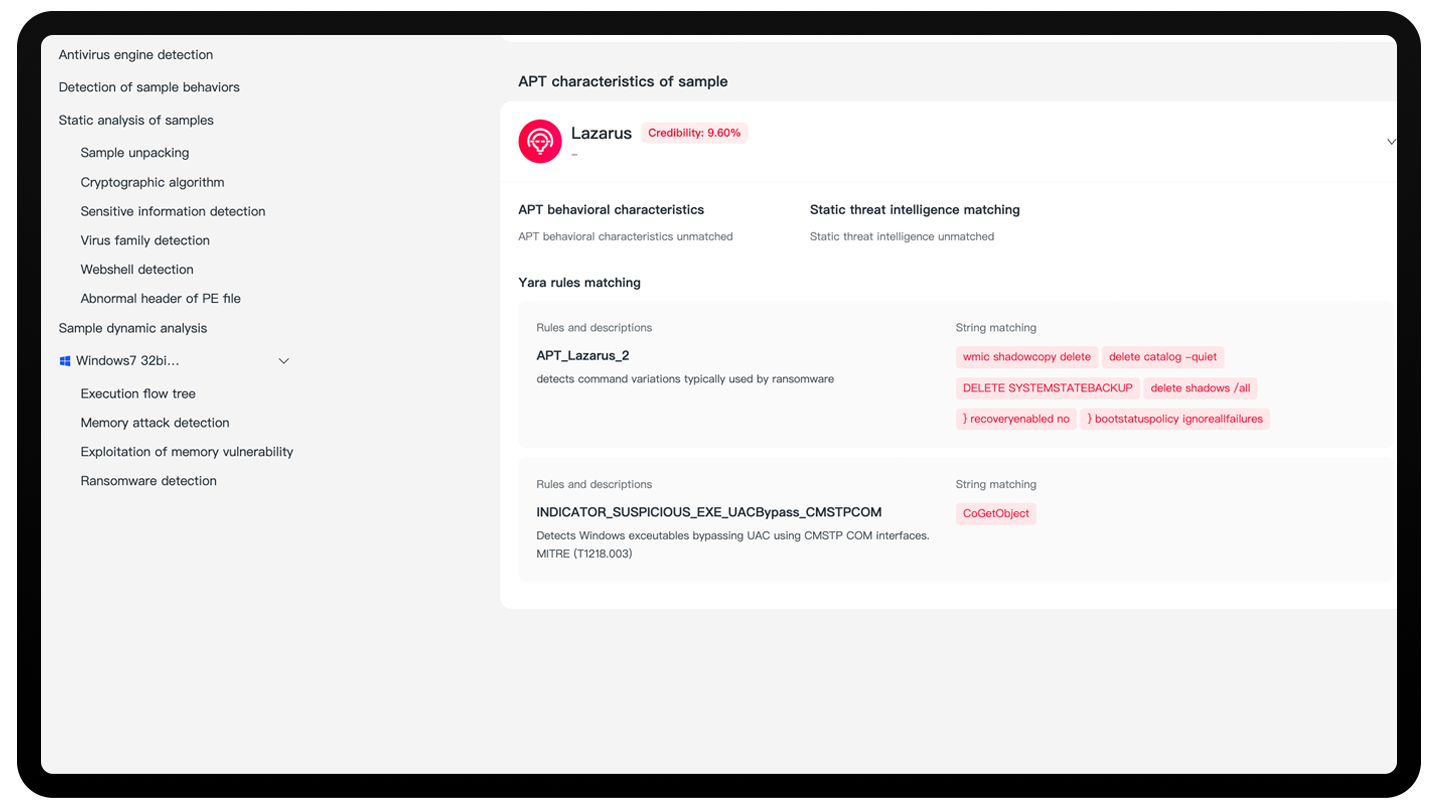
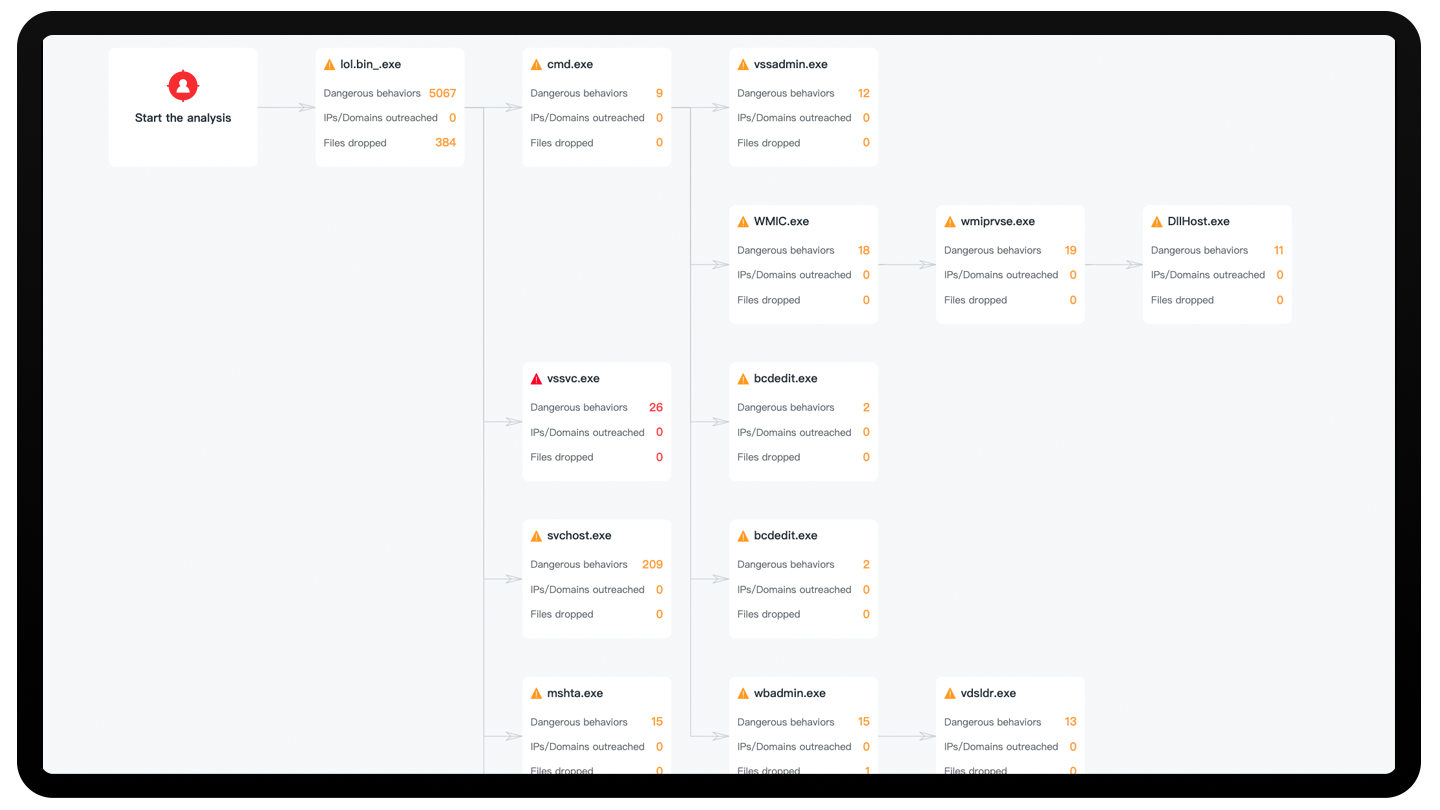
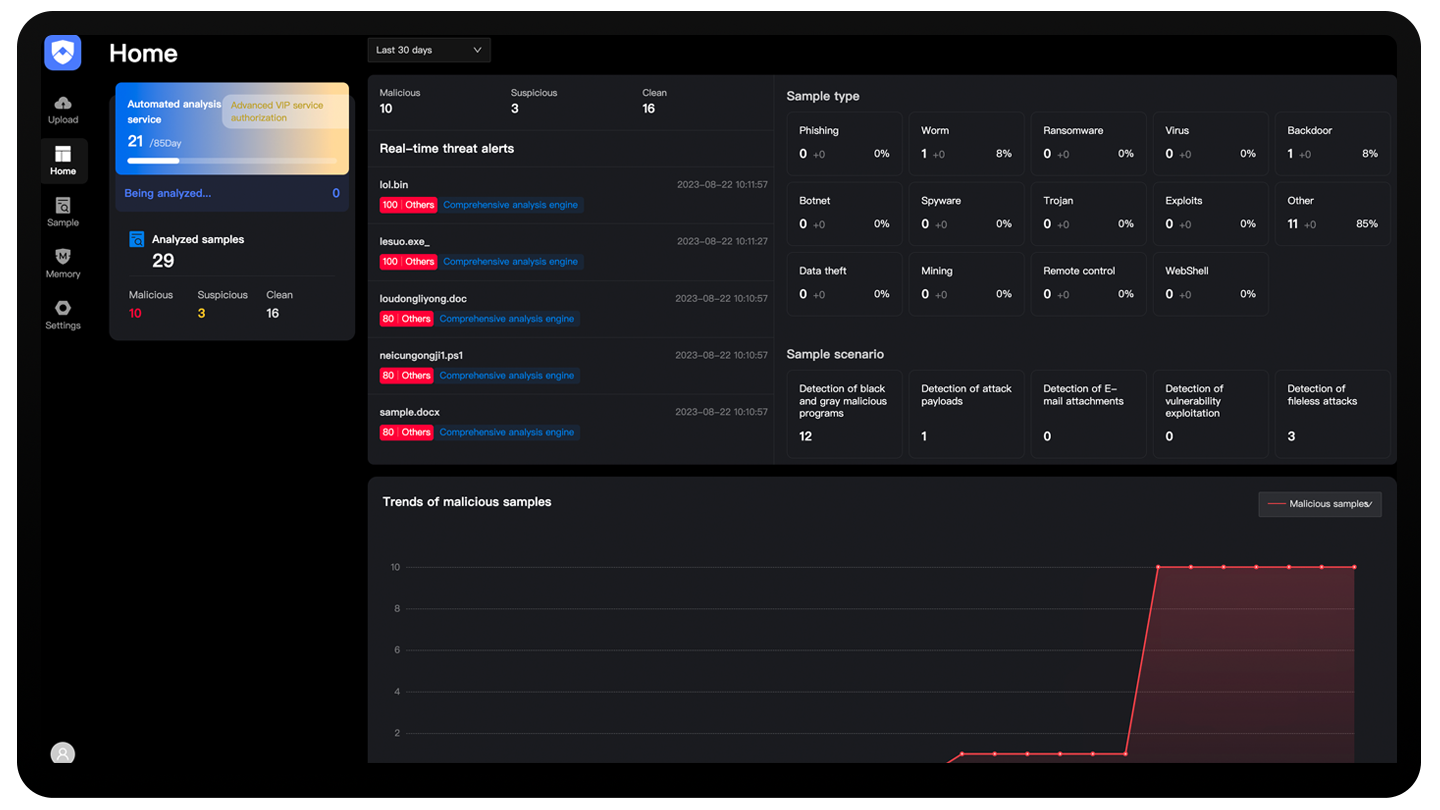
Intelligent Unpacking and Reverse Analysis: Intelligent detection of files and reverse analysis of packed files.
Memory-Based Vulnerability Exploit Behavior Detection: By conducting fine-grained monitoring of memory behaviors such as reads, writes, and executions, Anxinsec ATP can identify the attack behaviors of samples that exploit both known and unknown vulnerabilities.
Fileless Attack Exploit Detection: In-depth analysis of various script interpreters such as CMD, POWER SHELL, VBA, VBS, etc., to detect and alert on corresponding attack behaviors.
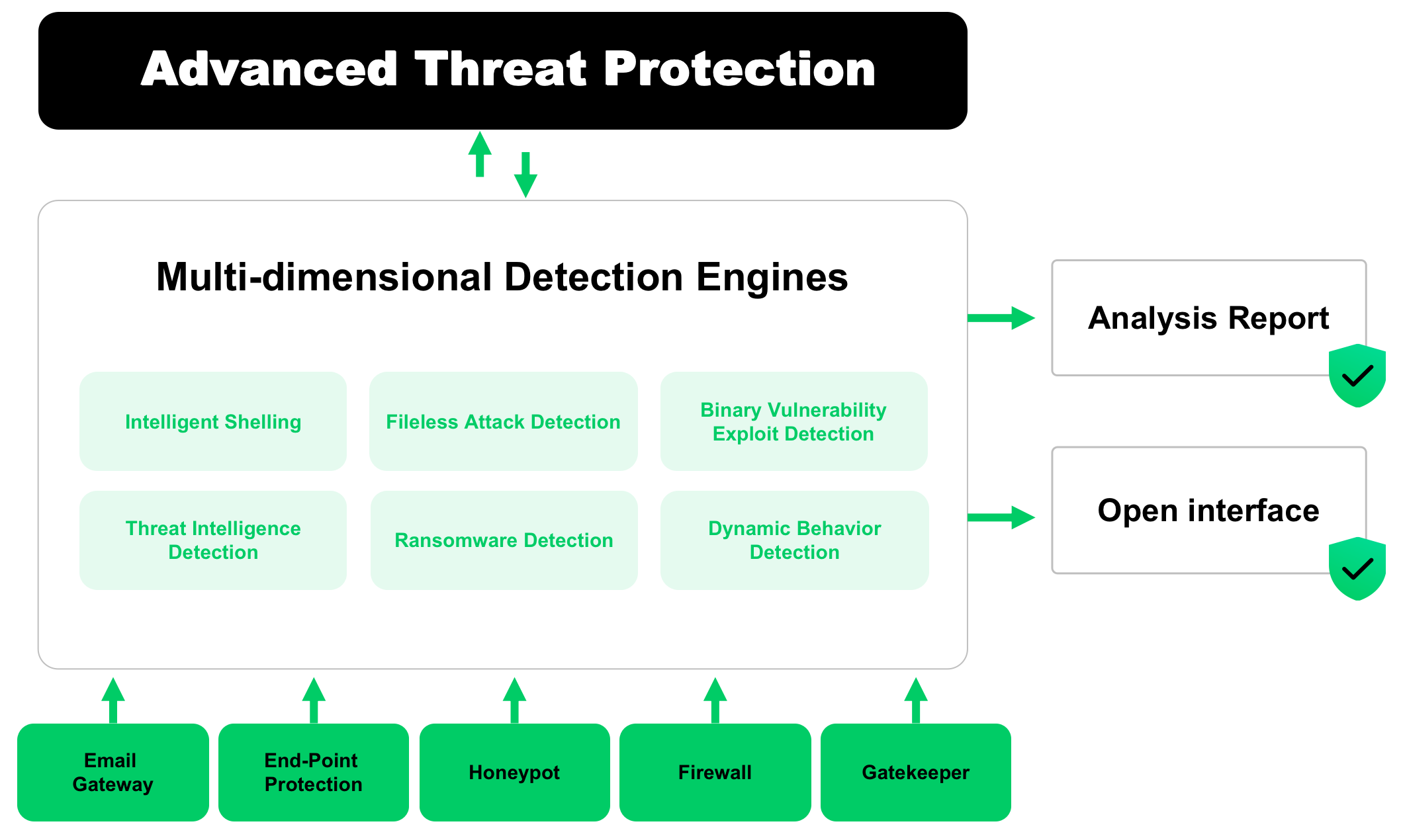
Intelligent Unpacking and Reverse Analysis: Intelligent detection of files and reverse analysis of packed files.
Memory-Based Vulnerability Exploit Behavior Detection: By conducting fine-grained monitoring of memory behaviors such as reads, writes, and executions, Anxinsec ATP can identify the attack behaviors of samples that exploit both known and unknown vulnerabilities.
Fileless Attack Exploit Detection: In-depth analysis of various script interpreters such as CMD, POWER SHELL, VBA, VBS, etc., to detect and alert on corresponding attack behaviors.