
























Safe desktop mode can lock the device in secure workspace, and reduce management cost of mobile devices, which supports the following settings
Force the mobile phone to work in secure workspace
Customize the applications in the workspace
Website Shortcut
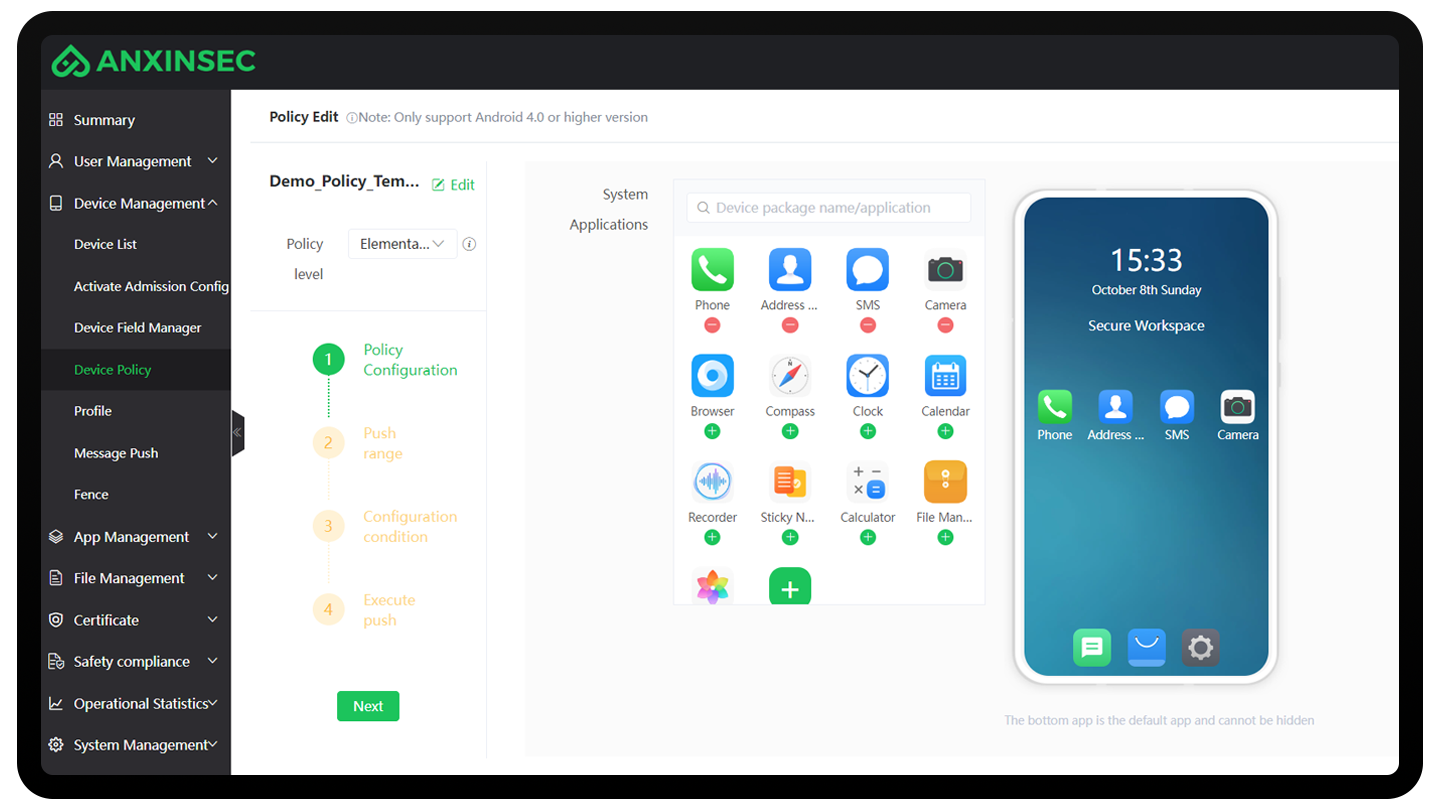
Safe desktop mode can lock the device in secure workspace, and reduce management cost of mobile devices, which supports the following settings
Force the mobile phone to work in secure workspace
Customize the applications in the workspace
Website Shortcut




















Time Based Fencing: Configurable time range based fencing
Region Based Fencing: Configurable regions based fencing
Electronic Fencing: Scan and retrieve identity number to enable fencing
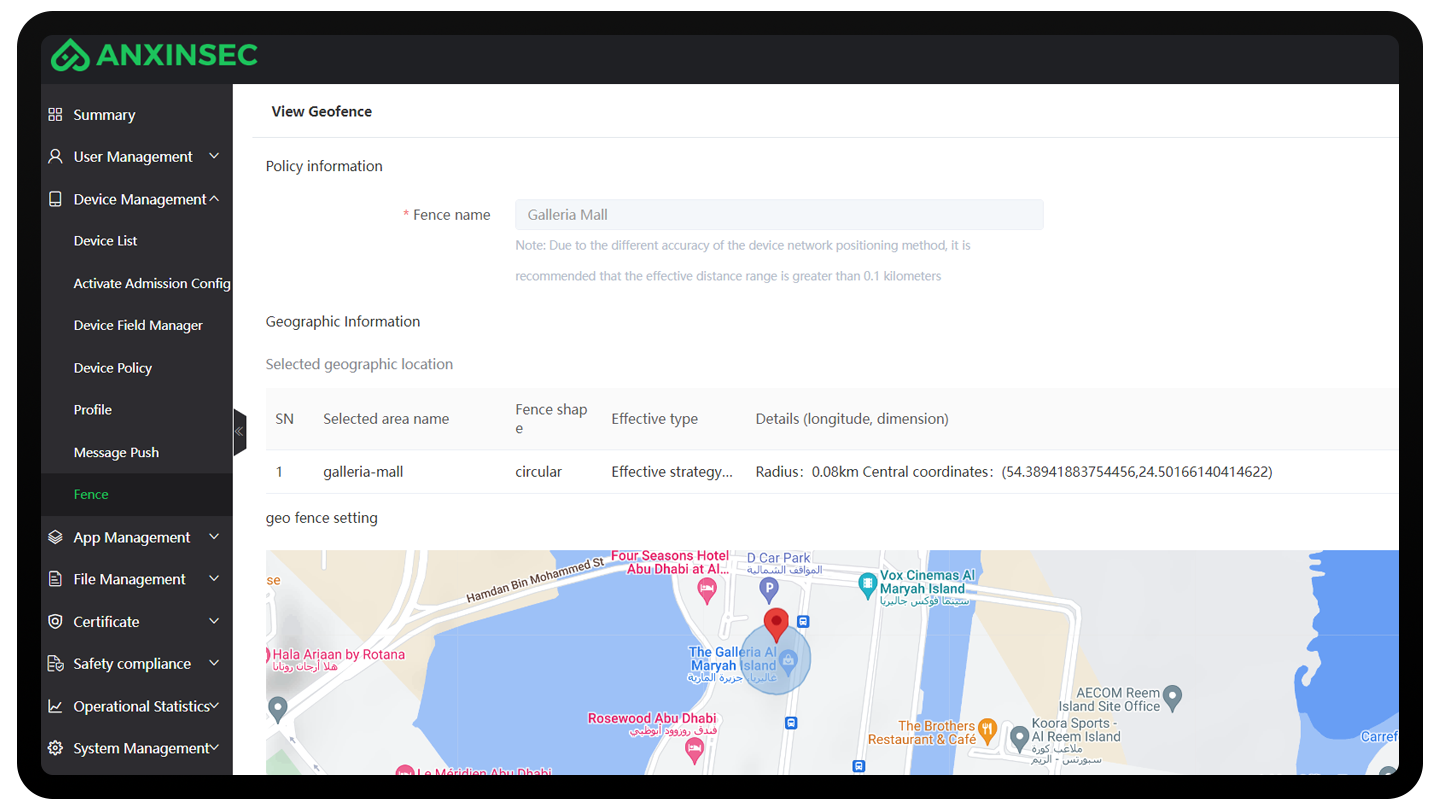
Time Based Fencing: Configurable time range based fencing
Region Based Fencing: Configurable regions based fencing
Electronic Fencing: Scan and retrieve identity number to enable fencing

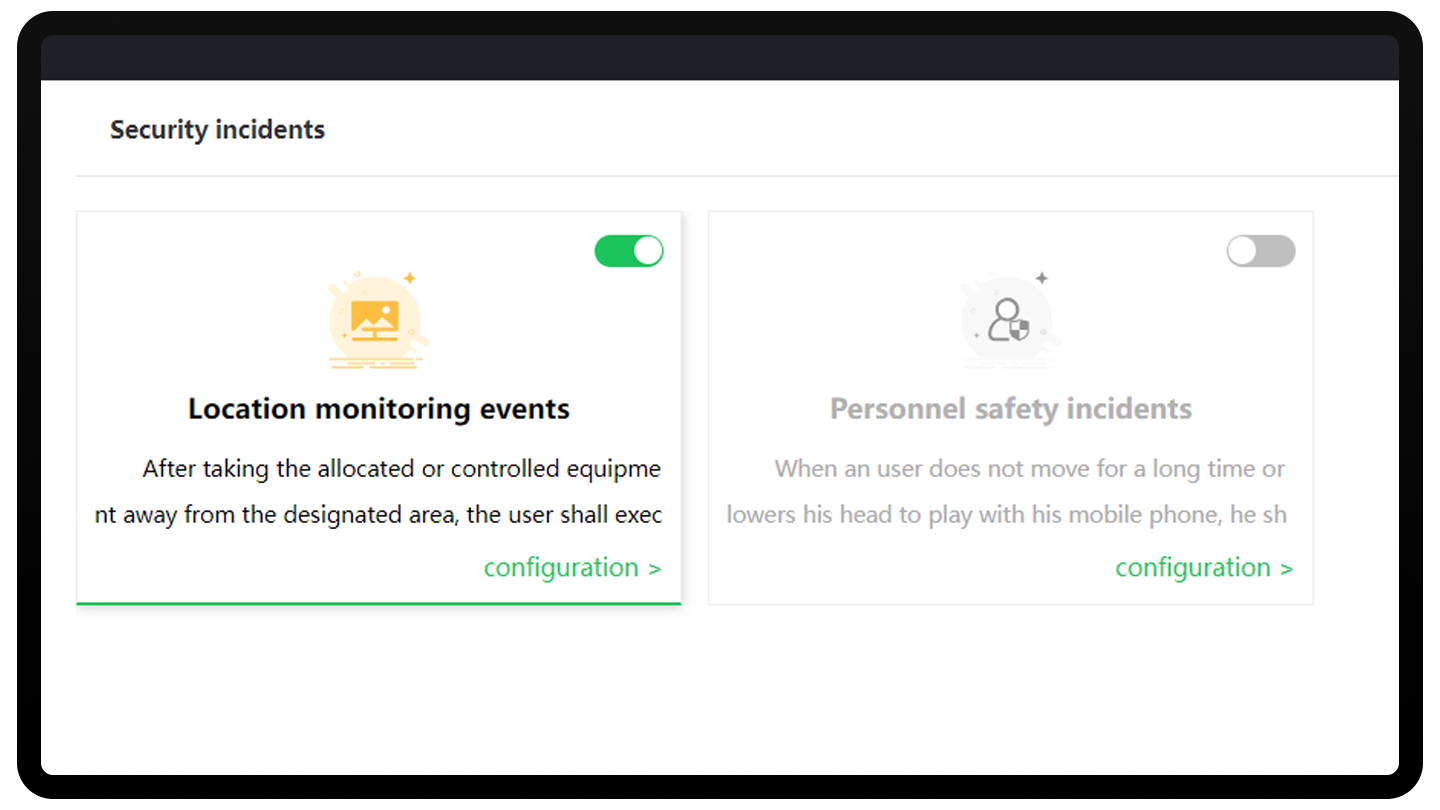
Compliance Policy: Develop separate compliance policies for Android/iOS
Compliance Action: Send an alarm when a device violation is detected

Compliance Policy: Develop separate compliance policies for Android/iOS
Compliance Action: Send an alarm when a device violation is detected

















