Advantage Capability
Closed-Loop Event Handling Logic
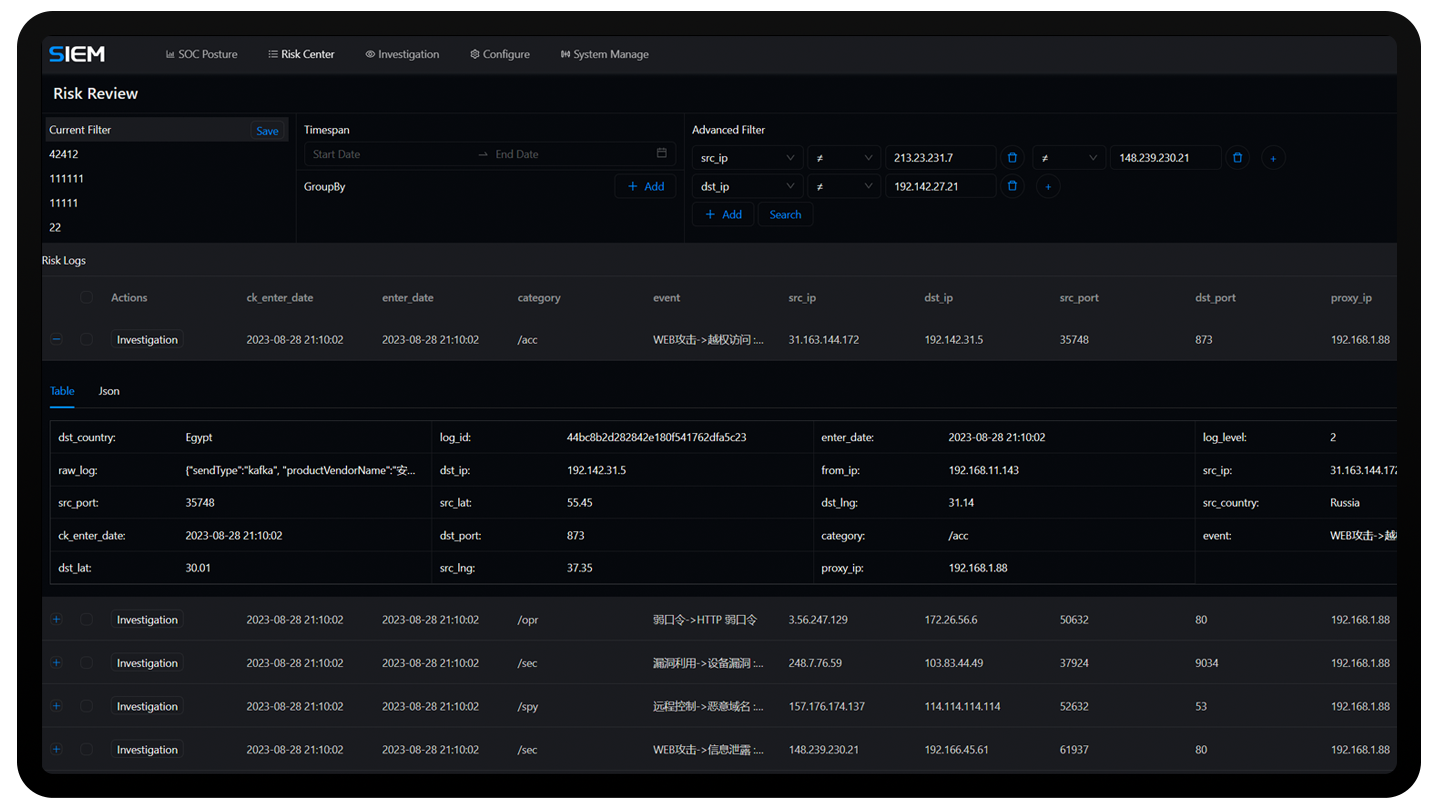
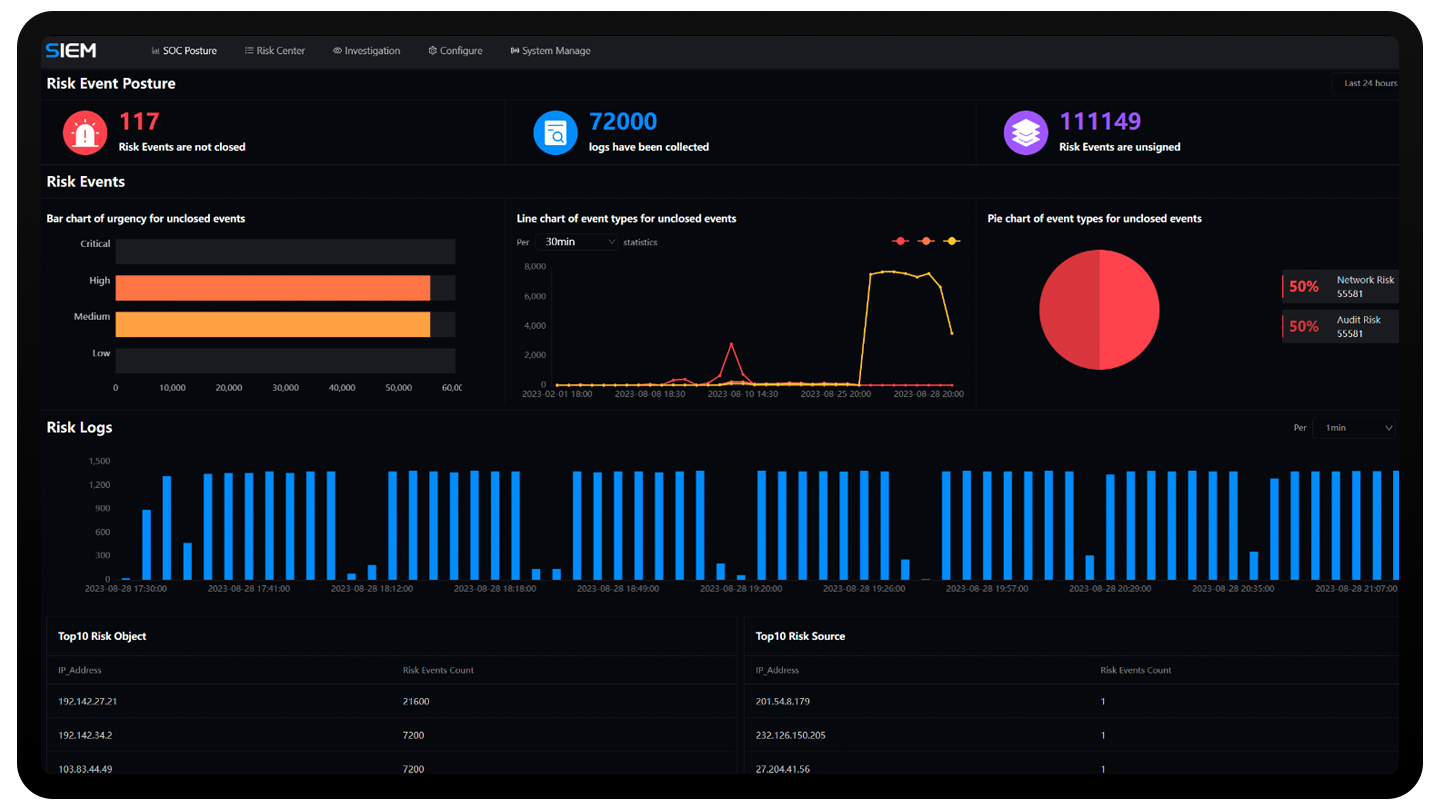
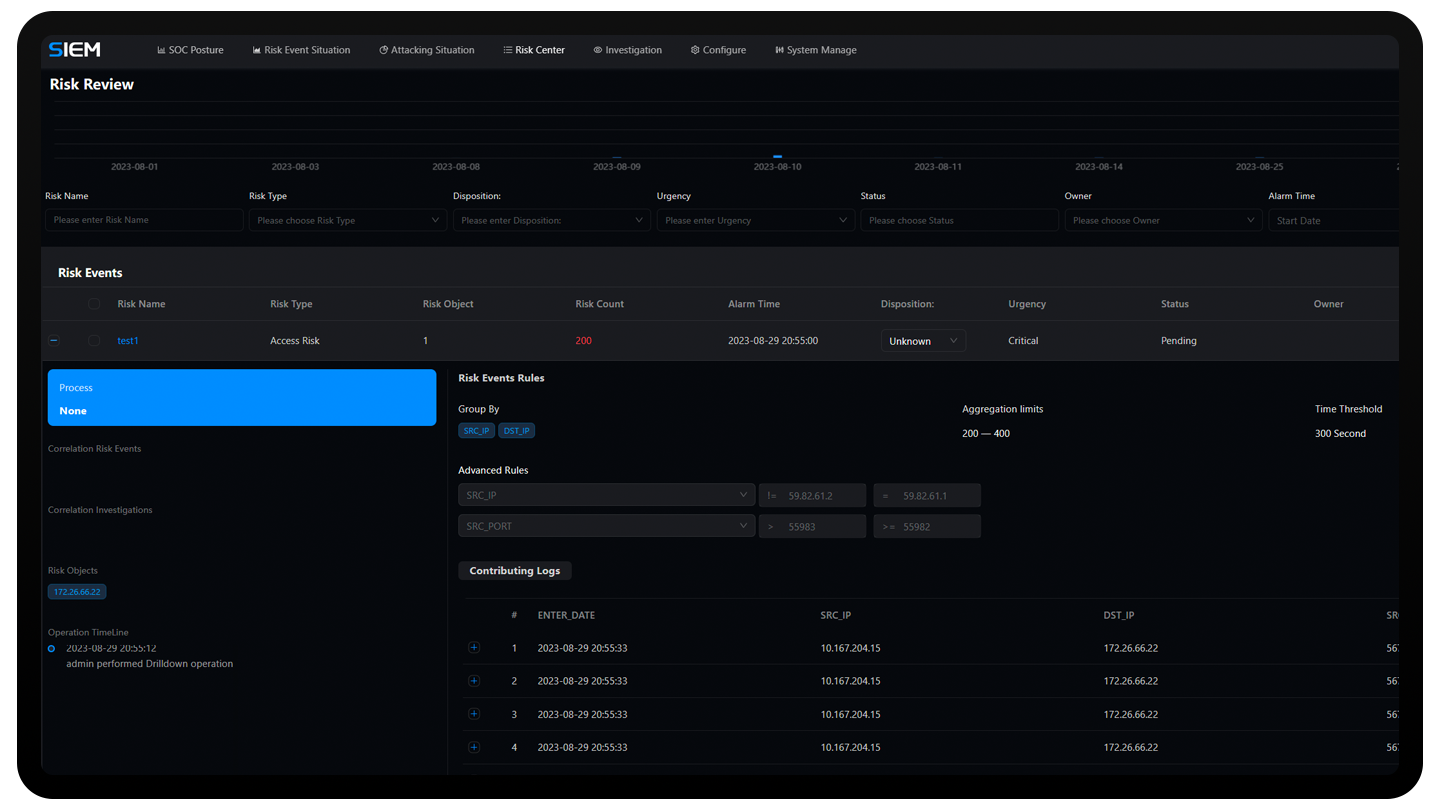
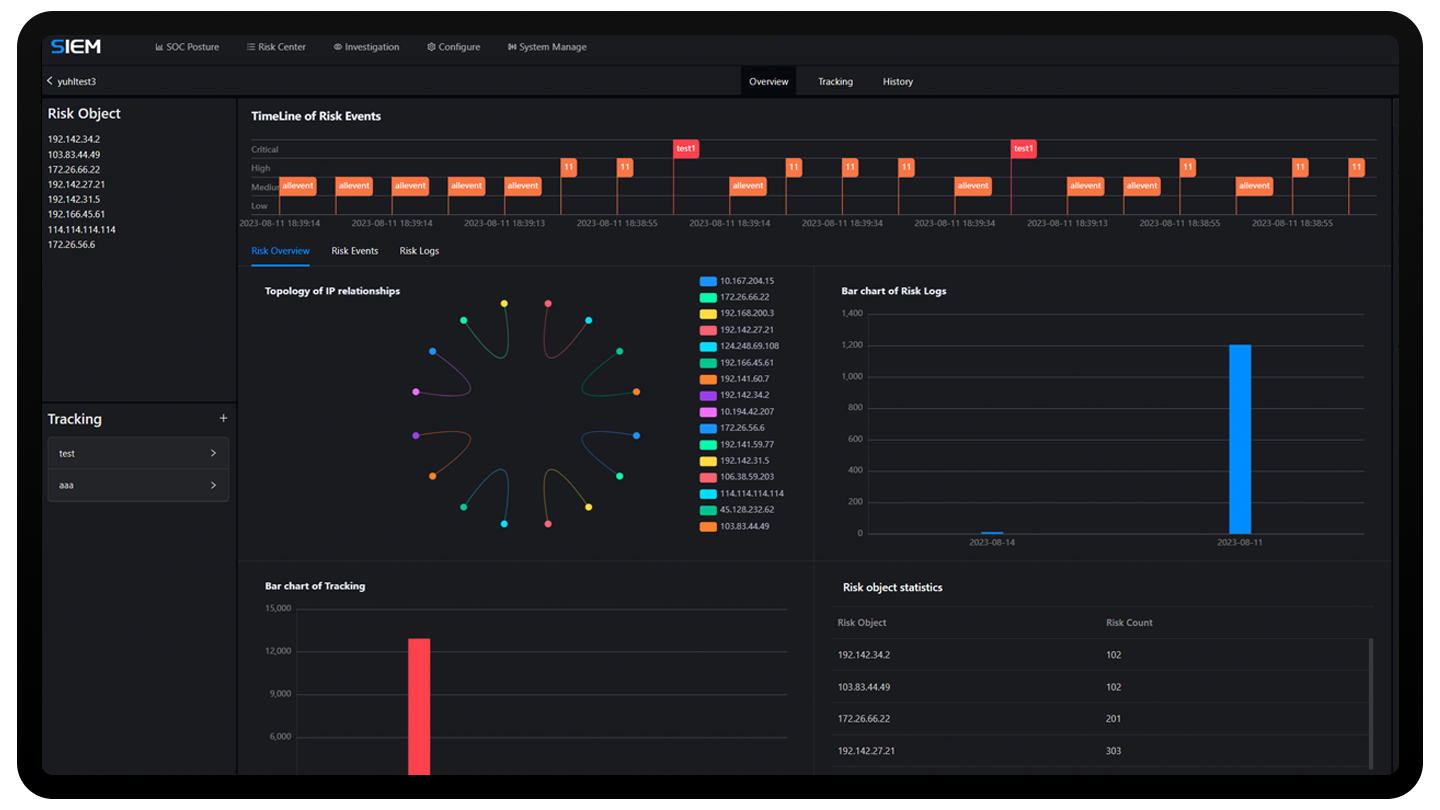
Anxinsec SOC offers a robust set of event handling functions, allowing you
to customize the workflow for security events and swiftly triage security incidents for further
investigation. Anxinsec SOC can assist you in efficiently managing and responding to security
incidents, as well as coordinating your security team's efforts.