Vulnerability Scanning:
Utilizing an agent-based continuous monitoring and analysis
mechanism, it can quickly and accurately detect system vulnerabilities by
comparing them
with an extensive vulnerability database.
Patch Management:
It offers a continuously updated patch library and agent-based probing
scans. It deeply examines critical updates for various software types within the
system,
including applications, kernel modules, installation packages, and intelligently
extracts patches that require immediate attention.
Risk Detection:
Real-time monitoring of system information such as memory, processes,
kernel modules, and files enables the timely identification of potential risks
within
the system.
Weak Password Detection:
Precisely identifies over a dozen types of application weak
passwords, including SSH system applications, Tomcat, MySQL, Redis, etc.. It
also
supports user-defined weak password vulnerability detection.

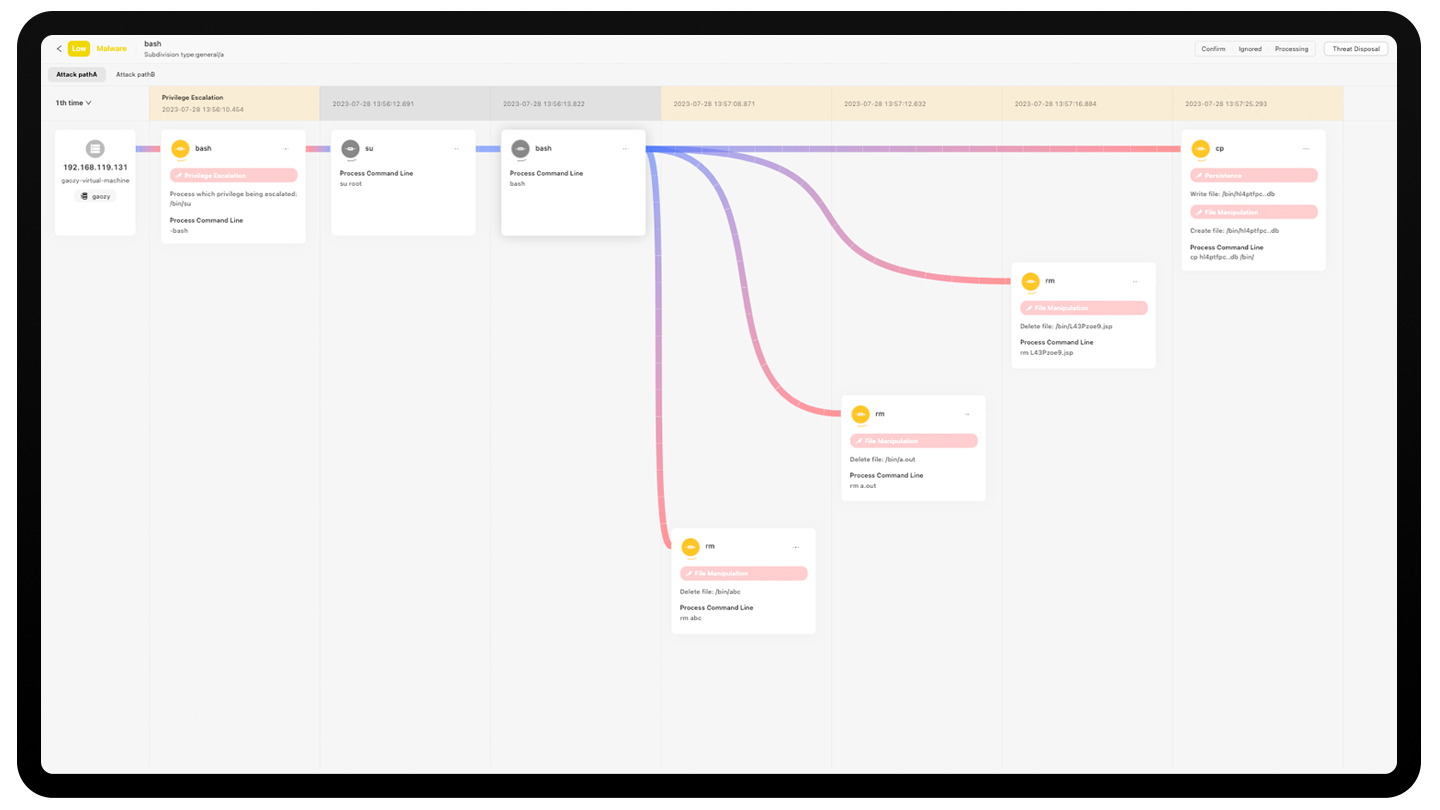
 Unique memory probe technology
Unique memory probe technology
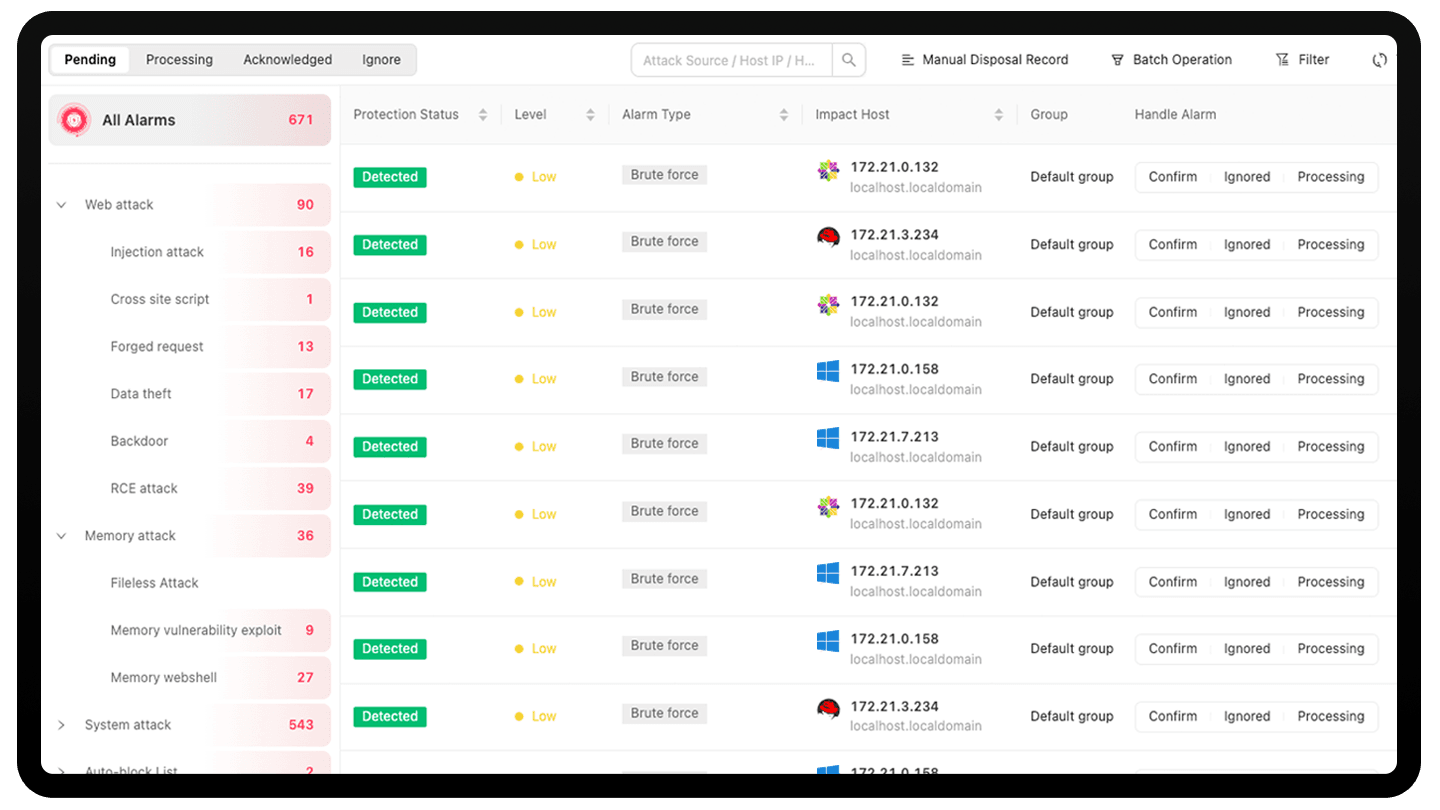


 Rich security operation and maintenance functions
Rich security operation and maintenance functions
















